In today’s hyper-connected world, where information flows freely across the vast landscape of the internet, the concept of security has taken on an entirely new dimension.
The advent of digital technology has brought about incredible advancements, revolutionizing the way we live, work, and communicate.
However, this digital age has also given rise to a host of threats and vulnerabilities, requiring innovative solutions to safeguard our digital assets and data.
One such solution that has gained prominence in recent years is the Digital Immune System, a robust defense mechanism designed to protect the cyber realm from ever-evolving threats.
The Digital Landscape: A Vulnerable Ecosystem
Before delving into the intricacies of the Digital Immune System, it’s crucial to understand the contemporary digital landscape.
We now live in a world where every aspect of our lives is influenced by digital technology.
From our personal communication to critical infrastructure, everything is interconnected through a complex web of networks and devices.
While this interconnectivity brings convenience and efficiency, it also exposes us to an array of cyber threats.
Cyber threats come in various forms, including malware, ransomware, phishing attacks, and data breaches.
These threats can have catastrophic consequences, ranging from financial losses and identity theft to national security breaches.
As the digital landscape continues to expand, so too does the surface area for potential attacks, making it imperative to develop effective defense mechanisms.
The Birth of the Digital Immune System
The concept of a Digital Immune System draws inspiration from the human body’s immune system, which defends against a multitude of pathogens and viruses.
In the digital realm, this concept has been adapted to protect against a wide array of cyber threats in a proactive and adaptive manner.
A Digital Immune System functions as an automated, intelligent, and ever-vigilant guardian of the digital world.
Understanding the Digital Immune System
The Digital Immune System operates on the principles of detection, analysis, and response, just like its biological counterpart.
However, it achieves these tasks through a combination of cutting-edge technologies and human expertise.
Detection:
The first line of defense in a Digital Immune System is the detection of potential threats.
This is achieved through a network of sensors and monitoring tools that constantly scan the digital environment for anomalies and suspicious activities.
On the otherhand These sensors can be compared to the body’s immune cells that identify foreign invaders.
Analysis:
Once a potential threat is detected, the Digital Immune System employs advanced analytics and machine learning algorithms to assess the nature and severity of the threat.
This analysis includes examining patterns, behavior, and known attack signatures, much like the way the human body’s immune system identifies pathogens.
Response:
Upon confirming a threat, the Digital Immune System initiates an appropriate response.
This may involve isolating affected systems, blocking malicious traffic, or deploying patches and updates to vulnerabilities.
Most Importantly This rapid response capability is essential to prevent the spread and impact of cyber threats.
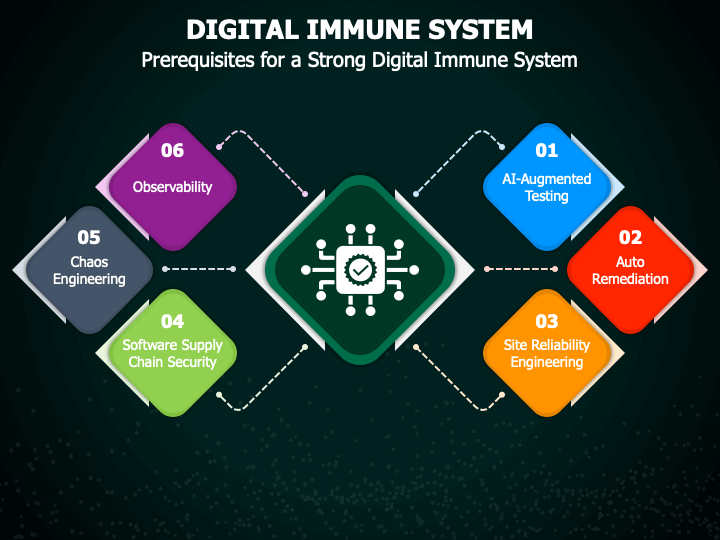
The Components of a Digital Immune System
A Digital Immune System is composed of several interconnected components, each playing a crucial role in defending the digital ecosystem.
These components work together seamlessly to create a robust defense mechanism. Let’s explore some of these key components:
Firewalls:
Firewalls act as the gatekeepers of a network, monitoring incoming and outgoing traffic and blocking any unauthorized or malicious connections.
And also Think of them as the digital equivalent of security personnel at a building’s entrance.
Intrusion Detection Systems (IDS):
Most Importantly IDS systems are designed to detect suspicious activity and potential threats within a network.
Moreover They analyze network traffic patterns to identify anomalies, alerting security teams to investigate further.
Antivirus Software:
Much like a vaccine, antivirus software protects against known threats by scanning files and software for malicious code. It’s an essential component in preventing malware infections.
Security Information and Event Management (SIEM) Systems:
SIEM systems collect and analyze data from various sources, including logs and security devicndes, and also to provide a holistic view of the digital environment.
Moreover This helps security teams identify and respond to threats more effectively.
Artificial Intelligence and Machine Learning:
AI and machine learning algorithms are employed to enhance threat detection by learning from past incidents and adapting to new attack patterns.
And They can identify evolving threats that traditional security measures might miss.
Incident Response Teams:
Importantly Human expertise remains a critical component of the Digital Immune System.
Highly skilled cybersecurity professionals form incident response teams that investigate and mitigate threats when detected.
The Evolution of the Digital Immune System
Much like the viruses and pathogens that adapt to evade the human immune system, cybercriminals continually evolve their tactics to bypass digital defenses.
As a result, the Digital Immune System must also evolve to keep pace with these threats. This evolution includes:
Machine Learning and AI Integration:
Increasing reliance on machine learning and artificial intelligence allows the Digital Immune System to adapt and respond to new and emerging threats in real-time.
Threat Intelligence Sharing:
Collaboration between organizations and sharing threat intelligence enables the Digital Immune System to learn from the experiences of others and proactively defend against similar threats.
Behavioral Analysis:
Analyzing the behavior of users and devices on a network helps identify unusual or suspicious activities, even when no known threat signatures are present.
Automation:
Automationof routine security tasks frees up cybersecurity professionals to focus on more complex.
And also strategic aspects of defense, such as threat hunting and vulnerability management.
Challenges and Ethical Considerations
While the Digital Immune System is a powerful tool in the fight against cyber threats.
it is not without its challenges and ethical considerations. Here are some important aspects to consider:
Privacy Concerns:
The monitoring and analysis required for threat detection may encroach on individual privacy.
Striking the right balance between security and privacy is an ongoing challenge.
False Positives:
Overly aggressive threat detection can lead to false positives, where legitimate activities are mistaken for threats. This can be disruptive and reduce user confidence.
Resource Constraints:
Smaller organizations may struggle to implement and maintain a robust Digital Immune System due to resource constraints.
Ethical Hacking:
The use of ethical hacking to test and improve the effectiveness of a Digital Immune System raises questions about the legality and ethics of such practices.
Conclusion:
The Digital Immune System
In a world where our lives are increasingly intertwined with digital technology, the Digital Immune System has emerged as a vital safeguard against cyber threats.
This intelligent and adaptive defense mechanism is essential in protecting our personal information, critical infrastructure, and national security.
As the digital landscape continues to evolve, so too must the Digital Immune System.
It requires ongoing development, investment, and collaboration to stay one step ahead of cybercriminals.
Furthermore, ethical considerations and privacy concerns must be addressed to ensure that the protection provided by the Digital Immune System is both effective and just.
A Necessity for the Digital Age
In conclusion, just as our bodies rely on a robust immune system to defend against illnesses, our digital world relies on the Digital Immune System to protect against cyber threats.
It is a testament to human ingenuity and innovation in the face of evolving challenges, and it will undoubtedly play a pivotal role in shaping the security landscape of the future.
As long as we continue to adapt and improve our digital defenses, the digital realm can remain a safer and more secure place for allImportantlt
